Supply chain risk management made easy
Identify risks across your supply chain with automated scans, data lookups and digital questionnaires. Made in EU.










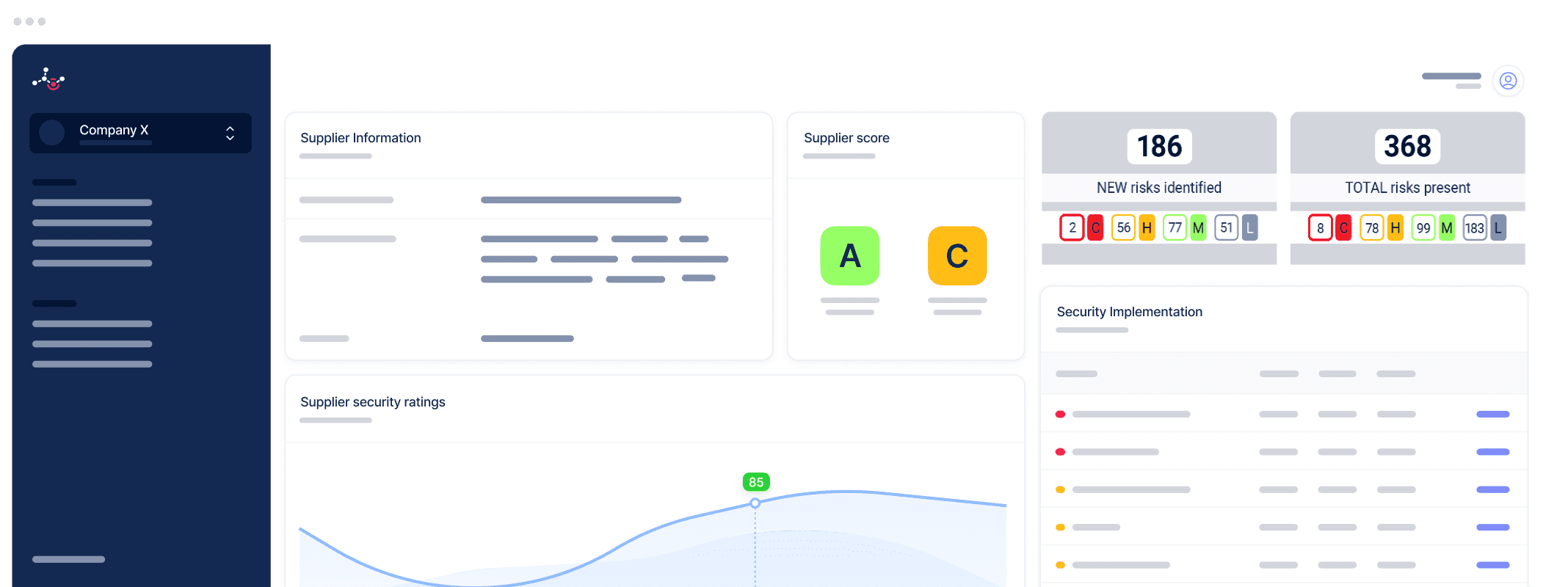
Automated vulnerability scanning and supply chain risk management
Questionnaire responses are often subjective and difficult to verify. Our attack surface scan identifies the presence of vulnerabilities in your critical suppliers' IT and network systems and complements the results of digital questionnaires for comprehensive supply chain risk management (also called third-party risk management or TPRM). Suppliers also have access to the data so they can take appropriate action.
+6.000.000 risks identified in customer supply chains
A
Average rating measured in the
Financial sector
C
Average rating measured in the
Pharmaceutical sector
D
Average rating measured in the
Manufacturing
Ceeyu Services
A powerful Software-as-a-Service risk identification and management platform that puts you in control of third-party risks.
Attack surface management (ASM)
Visualize security posture of your critical vendors, continuously scan for vulnerabilities, mitigate risks and avoid business downtime.
Third-party risk management (TPRM)
Understand security risks at key suppliers and partners, centralize assessments, and ensure business continuity
Digital Footprint Monitoring
Uncover your forgotten IT systems, unauthorized use of cloud services, unlawful publication of URLs or email addresses
Risk ratings
Understand risks and manage priorities thanks to a clear risk severity scoring system
Professional services
Outsource your third-party risk management administration, focus on risk management.
Why Ceeyu
Fully digital third-party risk management, complemented by automated security scans, in one user-friendly SaaS platform
Prevent cyber-attacks like ransomware, email phishing, or hacking of cloud environments and supply chain disruptions with Ceeyu’s risk assessment and management platform.
Understand the attack surface of your company, and your supply chain
Identify and manage risks of any kind (data breach, security, regulatory, ESG,...)
Actionable risk ratings
EU-based company & platform, data protected by EU law
Combine automated scans with questionnaire-based assessments
Customize to incorporate your own risk and procurement policies
Contributes to compliance with regulations like NIS2 and DORA, and frameworks like ISO 27001
Ceeyu features
EU made
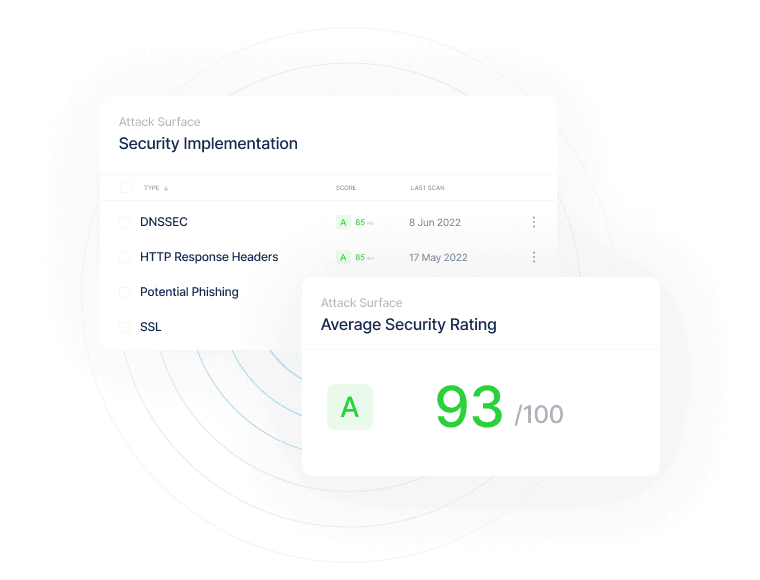
Automated security scans
Not just security
Intuitive & collaborative
SaaS
Assess the risks of your key suppliers and interact with them to remedy these.
Your suppliers' digital footprint can become a gateway for cybercriminals to enter your organization. And even if it doesn't, a security incident at one of your suppliers could disrupt your operations. With Ceeyu's Third Party Risk Management (TPRM) platform, you can detect cybersecurity risks at critical suppliers through attack surface scans (ASM). You can complement these with questionnaire-based audits, not only on security, but also on compliance, finance, 4th party risks, ....
Ensure business continuity
Comply with NIS2 and DORA
Get your ISO 27001, CIS or NIST certification
TPRM, without the hassle
"Ceeyu's SaaS platform automates many of the cumbersome processes that characterize TPRM, allowing us to reduce the time spent for our customers on this activity by 50%.”
Nick Prescot
Director CISO services

"Based on the risks identified by Ceeyu's SaaS platform, we can focus our resources on strengthening the security of our digital footprint and supply chain where needed."
Ruben Annemans
Head of Security at GlobalSign

“We chose to work with Ceeyu because it has the right feature set for risk assessments, nothing more and nothing less. This makes it far more efficient than other platforms that are full of features but difficult to work with.”
Christophe Rome
CISO

De Watergroep uses the Ceeyu platform for supplier risk due diligence in public tenders and periodically assess the risks at critical suppliers. They also use the Ceeyu platform for monitor the security risks in their own external Attack Surface in the context of NIS2. They also use Ceeyu’s Supplier onboarding service to lower the administrative work internally, and to speed up the assessment process.
Jeroen Roelandt
CISO

“Ceeyu has improved the way we manage supply chain risk as part of our ISO 27001 requirements. Its affordable platform is far more efficient than juggling Excel files and emails. With Ceeyu, we streamline our assessments and get clear visibility of our supplier risks, making ISO compliance and security management easier than ever before.”
Genkis Gurlek
ICT & Procurement manager

Ready to get started?
Book a call with our cybersecurity experts, or try it yourself, free of charge!